Blue Ant X4 Bluetooth speaker review: Price, sound quality, party mode, best bluetooth speaker? Worth it? | A multi-speaker party at the press of a button

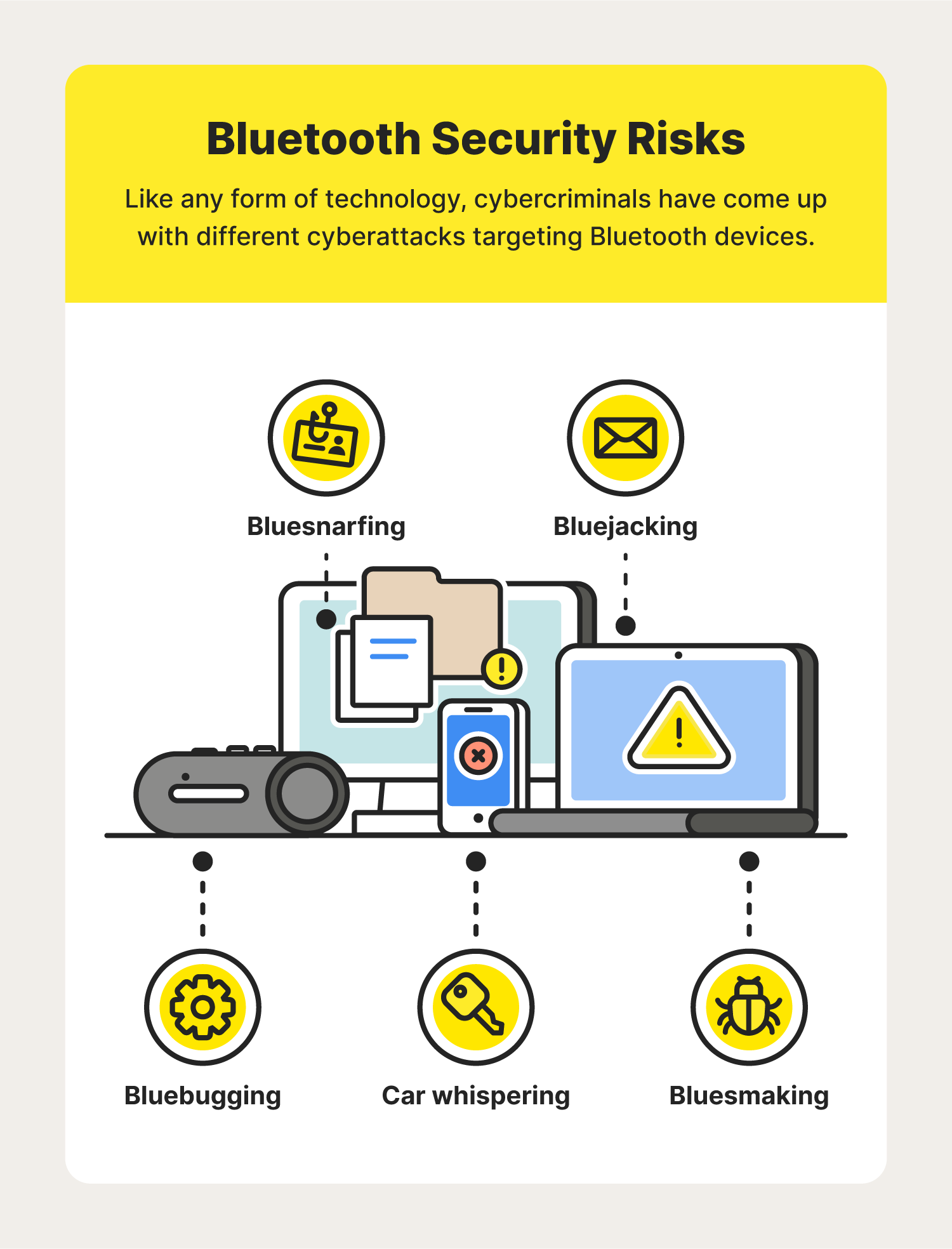
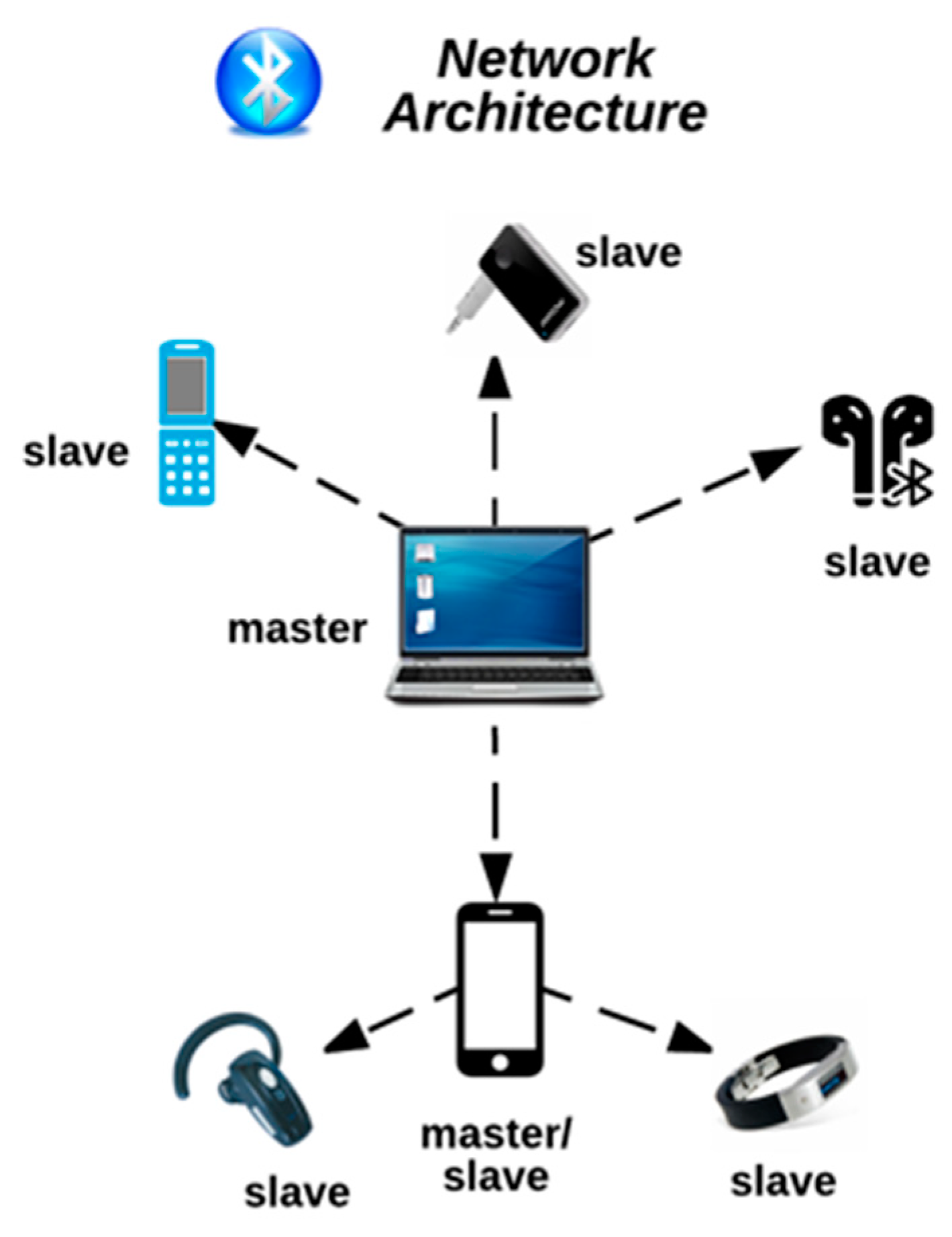
Revenge your neighbor's party by jamming any Bluetooth speaker. Creating a Bluetooth jammer with just 9 commands without any special hardware

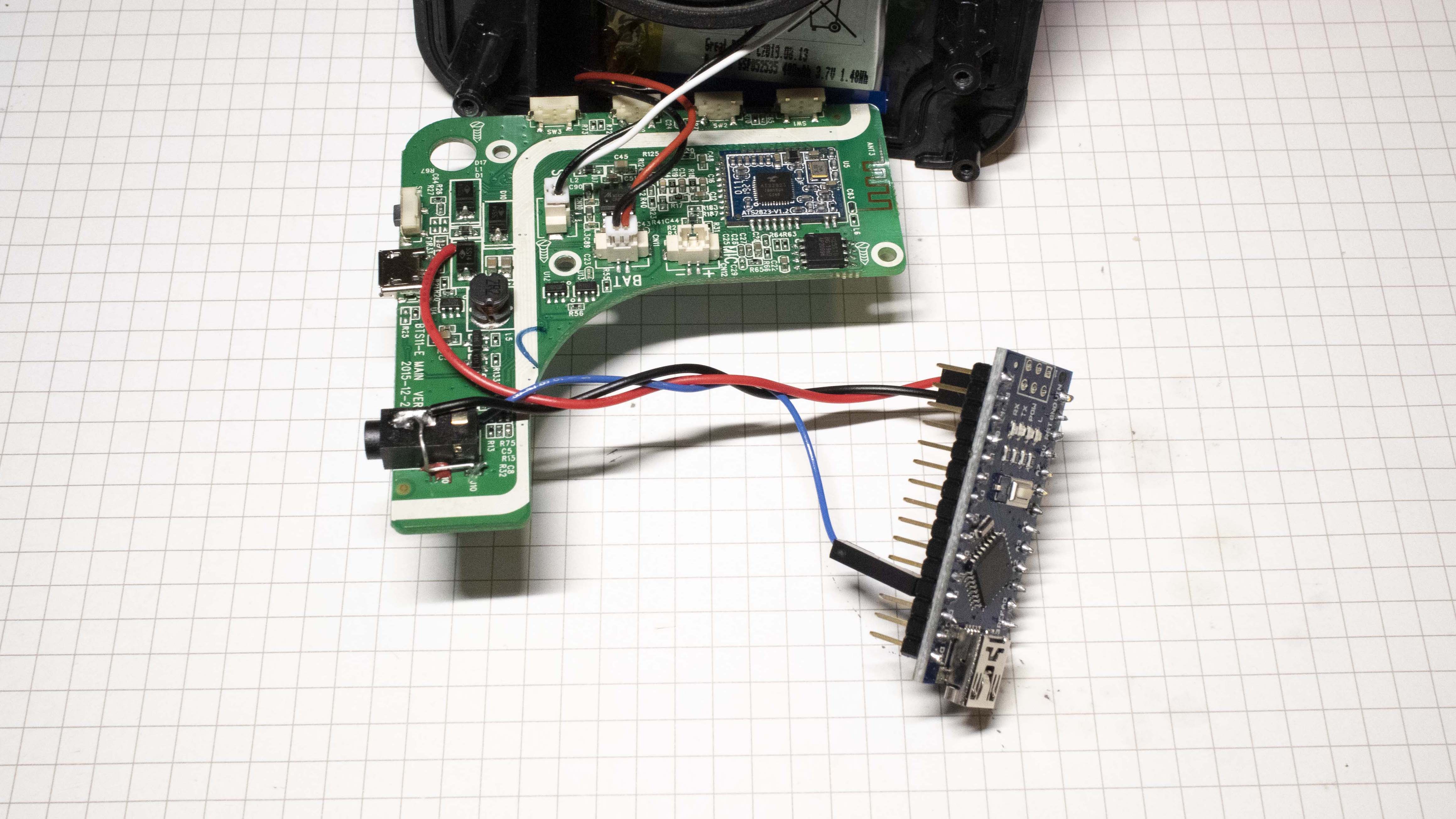
Hacking a Bluetooth Speaker || External Audio Jack | Bluetooth speaker, Small bluetooth speaker, Diy bluetooth speaker